You are here:
Secure Execution Processor
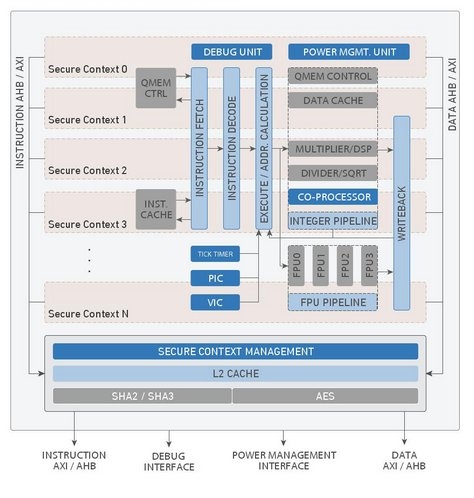
Geon Secure Execution Processor delivers secure code execution by supporting two secure contexts. All code and data belonging to a secure context is cryptographically isolated in main memory, so even complete software breach outside of secure context doen not compromise its security (confidentiality or integrity).
Cryptographic operations can be performed with single Keccak (SHA3) core or by combination of cryptographic hash primitives (SHA3 or SHA2) and symmetric ciphers.
Despite upgrades allowing for secure execution processing, the Geon processor maintains high configurability, performance and efficiency of the proven BA22. Performance is remaining in-line with BA22-CE.
The processor is already verified at system level and suitable for diverse security needs.
Cryptographic operations can be performed with single Keccak (SHA3) core or by combination of cryptographic hash primitives (SHA3 or SHA2) and symmetric ciphers.
Despite upgrades allowing for secure execution processing, the Geon processor maintains high configurability, performance and efficiency of the proven BA22. Performance is remaining in-line with BA22-CE.
The processor is already verified at system level and suitable for diverse security needs.
查看 Secure Execution Processor 详细介绍:
- 查看 Secure Execution Processor 完整数据手册
- 联系 Secure Execution Processor 供应商
Block Diagram of the Secure Execution Processor

Secure Execution Processor IP
- Secure Execution Processor
- Ultra-low power 32-bit processor with secure execution capability
- Low power 32-bit processor with secure execution capability
- Ultra-low power processor with RISC-V architecture possessing secure execution capability
- Secure-IC Securyzr(TM) Cyber Escort Unit IP provides real time detection of sero day attacks on processor
- 32-bit RISC core for secure applications



