You are here:
Secure Boot Hardware Engine
GEON-SBoot is an area-efficient, processor-agnostic hardware engine that protects SoC designs from booting with malicious or otherwise insecure code.
The security platform employs public-key cryptography (which stores no secret on-chip) to ensure that only unmodified firmware from a trusted source is used by the system. It also enables secure firmware updates over-the-air (OTA) and can prevent booting from revoked firmware versions. Optionally, GEON-SBoot can use symmetric encryption to protect the confidentiality of the firmware and prevent other devices from running firmware clones.
Designed for straightforward use in nearly any SoC, GEON-SBoot works with all modern architectures including RISC-V and ARM. It requires no software assistance from the host CPU, is independent of the memory types used, and uses standard interfaces. It further gives designers great flexibility in the boot control flow.
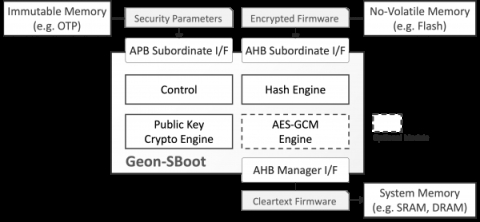
The isolated GEON-SBoot subsystem interfaces to the host system via three AMBA® ports: a subordinate AHB port for receiving the encrypted firmware, an AHB manager port for writing the authenticated, decrypted firmware to the system’s memory, and an APB subordinate port for receiving the security parameters. The security parameters (i.e., a hash of the public key and the symmetric key if used) are typically stored in immutable memory, constituting the root of trust. GEON-SBoot reports boot success or failure on its status register and via dedicated interrupt lines. It can optionally make its crypto accelerators available to the host system post-boot.
The GEON-SBoot core is production-proven and adheres to the industry’s best coding and verification practices to ensure trouble-free implementation in ASIC or FPGA technologies.
The security platform employs public-key cryptography (which stores no secret on-chip) to ensure that only unmodified firmware from a trusted source is used by the system. It also enables secure firmware updates over-the-air (OTA) and can prevent booting from revoked firmware versions. Optionally, GEON-SBoot can use symmetric encryption to protect the confidentiality of the firmware and prevent other devices from running firmware clones.
Designed for straightforward use in nearly any SoC, GEON-SBoot works with all modern architectures including RISC-V and ARM. It requires no software assistance from the host CPU, is independent of the memory types used, and uses standard interfaces. It further gives designers great flexibility in the boot control flow.
The isolated GEON-SBoot subsystem interfaces to the host system via three AMBA® ports: a subordinate AHB port for receiving the encrypted firmware, an AHB manager port for writing the authenticated, decrypted firmware to the system’s memory, and an APB subordinate port for receiving the security parameters. The security parameters (i.e., a hash of the public key and the symmetric key if used) are typically stored in immutable memory, constituting the root of trust. GEON-SBoot reports boot success or failure on its status register and via dedicated interrupt lines. It can optionally make its crypto accelerators available to the host system post-boot.
The GEON-SBoot core is production-proven and adheres to the industry’s best coding and verification practices to ensure trouble-free implementation in ASIC or FPGA technologies.
查看 Secure Boot Hardware Engine 详细介绍:
- 查看 Secure Boot Hardware Engine 完整数据手册
- 联系 Secure Boot Hardware Engine 供应商
Block Diagram of the Secure Boot Hardware Engine




