You are here:
SHA1, SHA2 Cryptographic Hash Cores
The SHA cores provide implementation of cryptographic hashes SHA-1 (core SHA1), SHA-2 (cores SHA2-256 and SHA2-512).
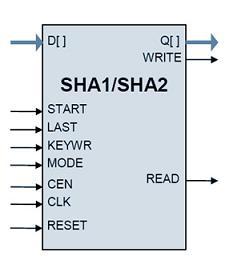
The cores utilize “flow-through” design that can be easily included into the data path of a communication system or connected to a microprocessor: the core reads the data via the D input and outputs the hash result via its Q output. Data bus widths for both D and Q are parameterized.
The design is fully synchronous and is available in both source and netlist form.
The cores utilize “flow-through” design that can be easily included into the data path of a communication system or connected to a microprocessor: the core reads the data via the D input and outputs the hash result via its Q output. Data bus widths for both D and Q are parameterized.
The design is fully synchronous and is available in both source and netlist form.
查看 SHA1, SHA2 Cryptographic Hash Cores 详细介绍:
- 查看 SHA1, SHA2 Cryptographic Hash Cores 完整数据手册
- 联系 SHA1, SHA2 Cryptographic Hash Cores 供应商
Block Diagram of the SHA1, SHA2 Cryptographic Hash Cores









