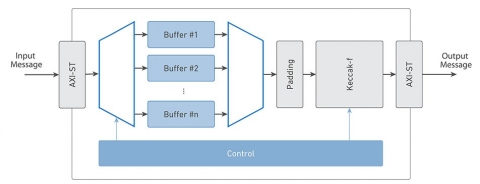
SHA-3 Secure Hash Function
Providing all four hash functions, Beyond’s SHA-3 hardware implementation has been optimized for applications that require fast block processing without excessive logic utilization. Simple input / output interface, adjustable bus widths and module properties, allow designers to seamlessly adapt the core to desired architectures, meeting demanding speed and area requirements.
查看 SHA-3 Secure Hash Function 详细介绍:
- 查看 SHA-3 Secure Hash Function 完整数据手册
- 联系 SHA-3 Secure Hash Function 供应商
Block Diagram of the SHA-3 Secure Hash Function