Securyzr integrated Security Services Platform (iSSP). Complete end-to-end security solution to supply, deploy and manage a fleet of devices from the cloud.
The Securyzr™ iSSP (integrated Security Services Platform) enables Secure-IC customers and partners to supply, deploy and manage the embedded security of their devices’ fleet all along their lifecycle. The Securyzr™ iSSP is an easy & trustful end-to-end solution for zero-touch security lifecycle services such as provisioning, firmware update, security monitoring & device identity management.
查看 Securyzr integrated Security Services Platform (iSSP). Complete end-to-end security solution to supply, deploy and manage a fleet of devices from the cloud. 详细介绍:
- 查看 Securyzr integrated Security Services Platform (iSSP). Complete end-to-end security solution to supply, deploy and manage a fleet of devices from the cloud. 完整数据手册
- 联系 Securyzr integrated Security Services Platform (iSSP). Complete end-to-end security solution to supply, deploy and manage a fleet of devices from the cloud. 供应商
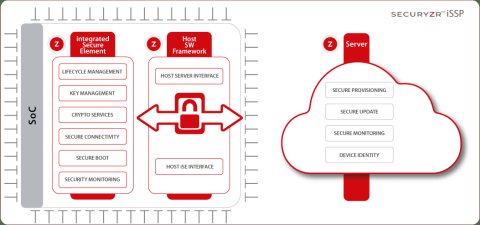
Block Diagram of the Securyzr integrated Security Services Platform (iSSP). Complete end-to-end security solution to supply, deploy and manage a fleet of devices from the cloud.
Video Demo of the Securyzr integrated Security Services Platform (iSSP). Complete end-to-end security solution to supply, deploy and manage a fleet of devices from the cloud.
This solution by Secure-IC runs on both public and private clouds and comes with a user-friendly web interface and software bridge for the devices to manage heterogeneous fleets of devices.
The Securyzr Server manages the different services for the platform and the business applications it hosts:
- Key provisioning to securely provision the chip devices with secret key across the supply chain,
- Firmware Update (FOTA/FUOTA) to securely provide chips with their software and then update them physically or over the air, to maintain their security level,
- Devices Monitoring and cyber intelligence to provide a proactive security service, retrieving cyber security logs from the chips, analyzing them and sending instructions back to the chip fleet if necessary,
- Devices Identity to guarantee trust from the chip to the cloud, to the devices, users and data through devices multi-factor authentication that allows resistance against impersonation, replay, and in the event of an initial compromise.
The security of the systems will be easily visualized through a Security Digital Twin.
security IP
- PCIe 5.0 Integrity and Data Encryption Security Module
- CXL 2.0 Integrity and Data Encryption Security Module
- RT-660-FPGA DPA-Resistant Hardware Root-of-Trust Security Processor for Govt/Aero/Defense FIPS-140
- RT-630-FPGA Hardware Root of Trust Security Processor for Cloud/AI/ML SoC FIPS-140
- RT-640 Embedded Hardware Security Module (HSM) for Automotive ASIL-B
- RT-645 Embedded Hardware Security Module (HSM) for Automotive ASIL-D






