You are here:
Secure-IC's Securyzr™ Active Shield: Protection against tampering Attack for all foundries processes
Attacks on digital circuits can occur when an attacker attempts to physically alter the device's internal components. These types of attacks are known as intrusive and can include actions such as probing or manipulating signals, adding or removing components, or modifying features on the chip.
To counteract these threats, Secure-IC has developed the Active Shield technology. This technology uses a protective mesh layer over the sensitive parts of the circuit, and actively monitors the mesh integrity for any signs of tampering. This countermeasure helps to safeguard the circuit's features and components, such as metal routing and transistors, from unauthorized access or modification through the front side of the device, such as:
Active monitoring
In order to further deter intrusive attacks, the mesh is actively monitored using random cryptographically generated patterns to detect integrity violations. By using this technology, modifying and rerouting the mesh becomes very costly as the attacker must reroute many wires to avoid detection. In addition, the data travelling through the shield mesh cannot be predicted by the attacker, because it is output by a cryptographic block cipher.
Active Shield technology relies on several submodules:
Ideal for
To counteract these threats, Secure-IC has developed the Active Shield technology. This technology uses a protective mesh layer over the sensitive parts of the circuit, and actively monitors the mesh integrity for any signs of tampering. This countermeasure helps to safeguard the circuit's features and components, such as metal routing and transistors, from unauthorized access or modification through the front side of the device, such as:
- Wire micro-probing to read or force an equipotential
- Wire cutting (e.g., alarms, entropy source disconnection from a true random number generator…)
- Wire re-routing
- Burnt fuses opening
- ROM Altering
Active monitoring
In order to further deter intrusive attacks, the mesh is actively monitored using random cryptographically generated patterns to detect integrity violations. By using this technology, modifying and rerouting the mesh becomes very costly as the attacker must reroute many wires to avoid detection. In addition, the data travelling through the shield mesh cannot be predicted by the attacker, because it is output by a cryptographic block cipher.
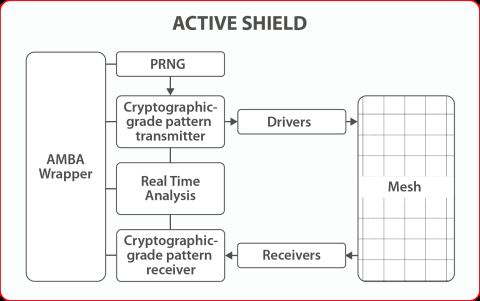
Active Shield technology relies on several submodules:
- A mesh created using a metal layer for wire routing
- Drivers and receivers used for electrical connection with the mesh
- A cryptographic-grade tamper detection module for monitoring the mesh integrity
Ideal for
- Active Shield IP is ideal for:
- Protection against Bus probing
- Protection against FIB attacks
- Protection against wire micro-probing to read or force an equipotential
- Protection against wire cutting (e.g., alarms, entropy source disconnection from a true random number generator)
- Protection against wire re-routing
- Protection against ROM altering
查看 Secure-IC's Securyzr™ Active Shield: Protection against tampering Attack for all foundries processes 详细介绍:
- 查看 Secure-IC's Securyzr™ Active Shield: Protection against tampering Attack for all foundries processes 完整数据手册
- 联系 Secure-IC's Securyzr™ Active Shield: Protection against tampering Attack for all foundries processes 供应商
Block Diagram of the Secure-IC's Securyzr™ Active Shield: Protection against tampering Attack for all foundries processes




