You are here:
Secure Hash Algorithm-3 (SHA-3)
CYB- SHA3 implements Secure Hash Algorithm-3 (SHA-3) family of
functions on binary data with the NIST FIPS 202 Standard. It supports
cryptographic hash functions (SHA3-224, SHA3-256, SHA3-384, and
SHA3-512). SHA-3 can be directly substituted for SHA-2 in current
applications and significantly improve the robustness of NIST's overall
hash algorithm toolkit. It provides two versions of SHA3 IP: SHA3 hash
engine and SHA3 hash engine with input buffer and padding logic. It is
flexible to select different versions based on various requirements.
CYB-SHA3 is an ideal solution for wireless communication, payment
products and IoT devices with high implementation performance. It is
fastly and easily integrated into ASIC and FPGA applications.
functions on binary data with the NIST FIPS 202 Standard. It supports
cryptographic hash functions (SHA3-224, SHA3-256, SHA3-384, and
SHA3-512). SHA-3 can be directly substituted for SHA-2 in current
applications and significantly improve the robustness of NIST's overall
hash algorithm toolkit. It provides two versions of SHA3 IP: SHA3 hash
engine and SHA3 hash engine with input buffer and padding logic. It is
flexible to select different versions based on various requirements.
CYB-SHA3 is an ideal solution for wireless communication, payment
products and IoT devices with high implementation performance. It is
fastly and easily integrated into ASIC and FPGA applications.
查看 Secure Hash Algorithm-3 (SHA-3) 详细介绍:
- 查看 Secure Hash Algorithm-3 (SHA-3) 完整数据手册
- 联系 Secure Hash Algorithm-3 (SHA-3) 供应商
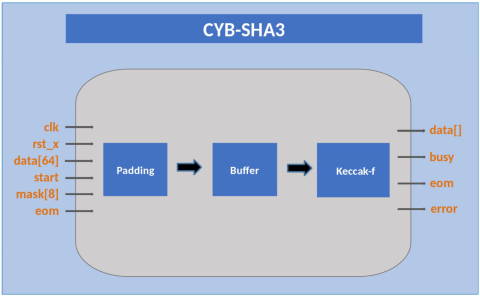
Block Diagram of the Secure Hash Algorithm-3 (SHA-3)

SHA3 IP
- Secure-IC Securyzr™ Tunable Cryptography solutions with embedded side-channel protections: AES - SHA2 - SHA3 - PKC - RSA - ECC - ML-KEM - ML-DSA - XMSS - LMS - SM2 - SM3 - SM4 - Whirlpool - CHACHA20 - Poly1305
- Secure-IC's Securyzr™ Tunable Hash (SHA3) Hardware accelerator
- SHA-3 Secure Hash Function Core
- Secure-IC's Securyzr™ SHA-3 Crypto Engine
- SHA-3 Crypto IP Core
- SHA3 IP Core



