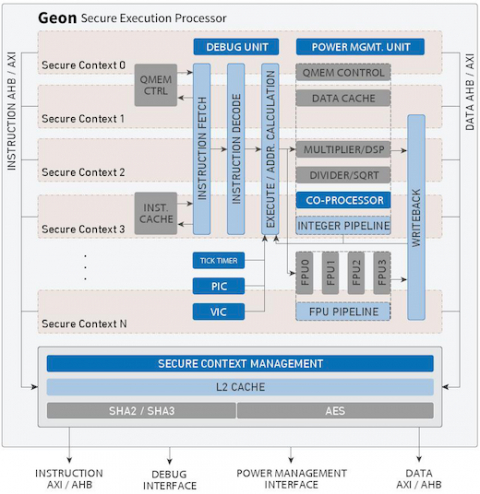
Secure Execution Processor
Geon benefits from the extreme code density of the BA2xTM ISA, and employs advanced power management to further lower CPU and memory subsystem power consumption. It can be licensed without volume-based royalty fees.
Secure Execution with Geon
Geon addresses two fundamental security risks of modern SoC designs. First, it protects against breaches of confidentiality and integrity when firmware is stored outside or transferred to the processor. Geon does this by using authenticated encryption: code and data are only decrypted and checked for integrity at fetch time within the processor, and therefore are protected while they reside on the system memory or while being transferred to the processor.
Second, Geon protects against breaches of sensitive code and data from compromised software threads. For this it assigns address spaces and processor units to just one of the multiple secure execution contexts, and uses a separate set of encryption keys per execution context for the code and data encryption. In this manner, even a complete breach of a software thread in one execution context fails to compromise the data and code of the other contexts.
查看 Secure Execution Processor 详细介绍:
- 查看 Secure Execution Processor 完整数据手册
- 联系 Secure Execution Processor 供应商
Block Diagram of the Secure Execution Processor