You are here:
Secure-IC Securyzr(TM) Cyber Escort Unit IP provides real time detection of sero day attacks on processor
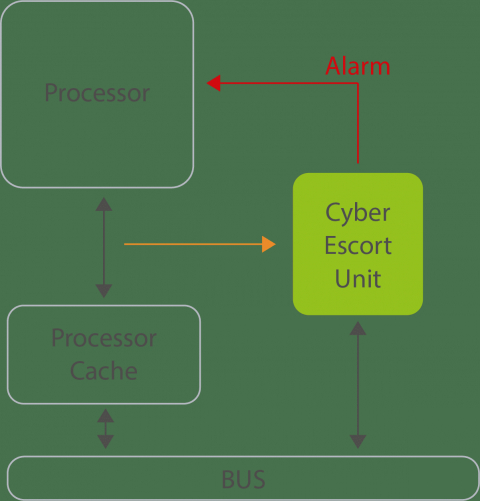
Secure-IC Securyzr™ Cyber Escort Unit is designed to fill the security gap between software cybersecurity and hardware by escorting step by step the program execution to achieve high execution performances in a secure way, allowing advantageously real-time detection of zero-day attacks. Unique on the market, this product builds the foundation for hardware-enabled cybersecurity.
It is the only tool on the market that comprises technologies for detecting and deceiving cyberattacks. This technology acts on-the-fly. Precisely, Cyber Escort Unit (CyberEU in short) is a two-fold technology aiming to protect against four threats:
Those threats represent a large amount of vulnerabilities encountered in practice. For instance, more than a quarter of the attacks on Supervisory control and Data Acquisition systems (Figure 1) consist in improper restrictions of operations within the bounds of a memory buffer.
It is the only tool on the market that comprises technologies for detecting and deceiving cyberattacks. This technology acts on-the-fly. Precisely, Cyber Escort Unit (CyberEU in short) is a two-fold technology aiming to protect against four threats:
- Return oriented programming (ROP), Jump Oriented Programming (JOP): The attacker reuses chunks of code to assemble a malicious program as a patchwork.
- Stack Smashing, by exploiting a buffer over run or integer under-or-overflow etc.: the attacker crafts some fake stack frames in order to change the program context.
- Executable Code Modification, Overwrite: the attacker manages to change the genuine program into a malicious program.
- Control Flow hijacking: the attacker manipulates the program so that it calls an illicit function, or it takes an illicit branch.
Those threats represent a large amount of vulnerabilities encountered in practice. For instance, more than a quarter of the attacks on Supervisory control and Data Acquisition systems (Figure 1) consist in improper restrictions of operations within the bounds of a memory buffer.
查看 Secure-IC Securyzr(TM) Cyber Escort Unit IP provides real time detection of sero day attacks on processor 详细介绍:
- 查看 Secure-IC Securyzr(TM) Cyber Escort Unit IP provides real time detection of sero day attacks on processor 完整数据手册
- 联系 Secure-IC Securyzr(TM) Cyber Escort Unit IP provides real time detection of sero day attacks on processor 供应商
Block Diagram of the Secure-IC Securyzr(TM) Cyber Escort Unit IP provides real time detection of sero day attacks on processor

security ip IP
- PCIe 5.0 Integrity and Data Encryption Security Module
- CXL 2.0 Integrity and Data Encryption Security Module
- RT-660-FPGA DPA-Resistant Hardware Root-of-Trust Security Processor for Govt/Aero/Defense FIPS-140
- RT-630-FPGA Hardware Root of Trust Security Processor for Cloud/AI/ML SoC FIPS-140
- RT-640 Embedded Hardware Security Module (HSM) for Automotive ASIL-B
- RT-645 Embedded Hardware Security Module (HSM) for Automotive ASIL-D








