MACsec - Extreme-speed - Security Protocol
The underlying cryptographic engines in the MACsec solutions are powered by Xiphera's in-house designed AES-GCM Intellectual Property (IP) cores.
Xiphera is offering three MACsec variants: MACsec Balanced, MACsec High-Speed, and MACsec Extreme-Speed
查看 MACsec - Extreme-speed - Security Protocol 详细介绍:
- 查看 MACsec - Extreme-speed - Security Protocol 完整数据手册
- 联系 MACsec - Extreme-speed - Security Protocol 供应商
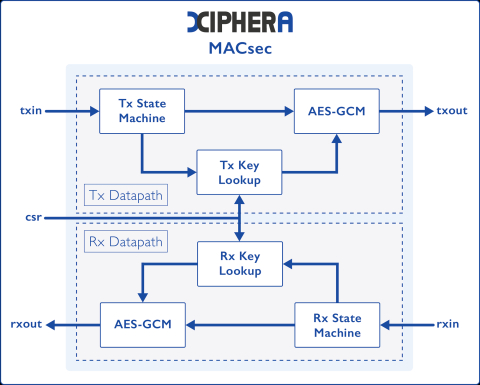
Block Diagram of the MACsec - Extreme-speed - Security Protocol
Video Demo of the MACsec - Extreme-speed - Security Protocol
How to secure device communications and the rapidly growing Internet of Things?
This webinar presents implementations of MACsec, IPsec, and TLS on hardware devices, and explores the similarities and differences between the three security protocols. We will hear insights and guidance in the implementation decisions facing designers and architects responsible for ensuring secure connectivity.








